Using Single-Sign-On with RIA Applications (Magic xpa 4.x)
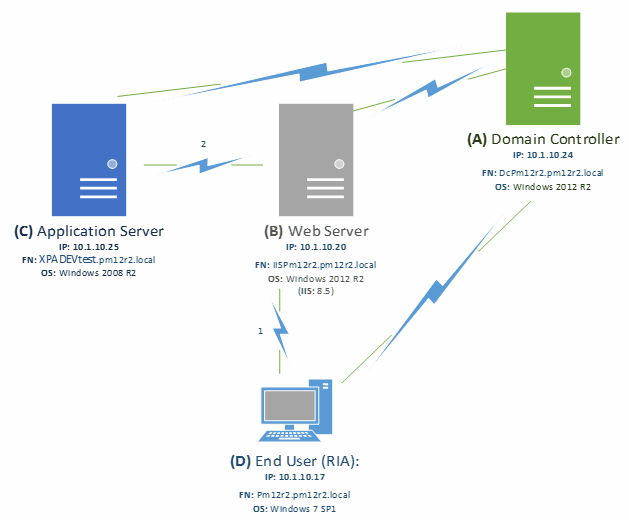
This technical note describes the steps required to use Windows Authentication with Kerberos, to authenticate a RIA application (D in the diagram below) to IIS (B in the diagram below) and the Magic xpa server (C in the diagram below).
On the Web Server machine (B in the diagram above):
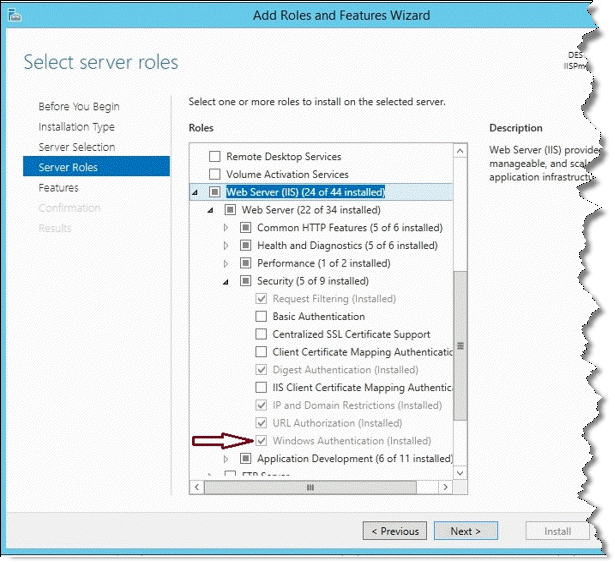
1. Verify that the Windows Authentication feature is installed:
-
Go to Programs and Features. Click the Turn the Windows features on or off entry. The Add Roles and Features Wizard opens.
-
From the Select installation type screen, select Role-based or feature-based installation and then click Next.
-
From the Server Pool, select your server, and click Next.
-
Expand Web Server (IIS) > Web Server > Security. Check that the Windows Authentication (Installed) option is selected. If it is not selected, check this option, click Next twice and then click Install.
2. Open the IIS Manager, expand the Sites folder until you reach MagicScripts, and select it.
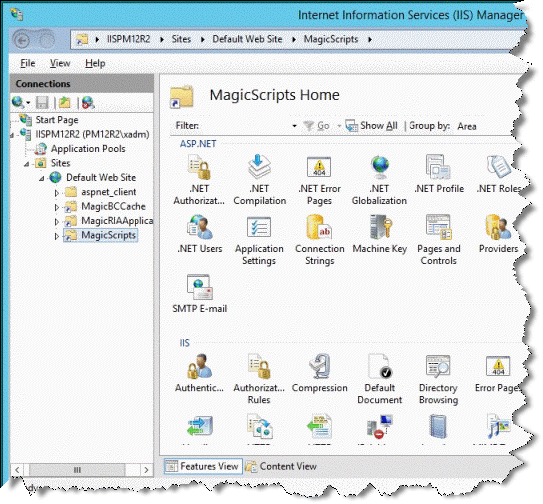
3. From the Features View (central part of IIS GUI), double click on Authentication.
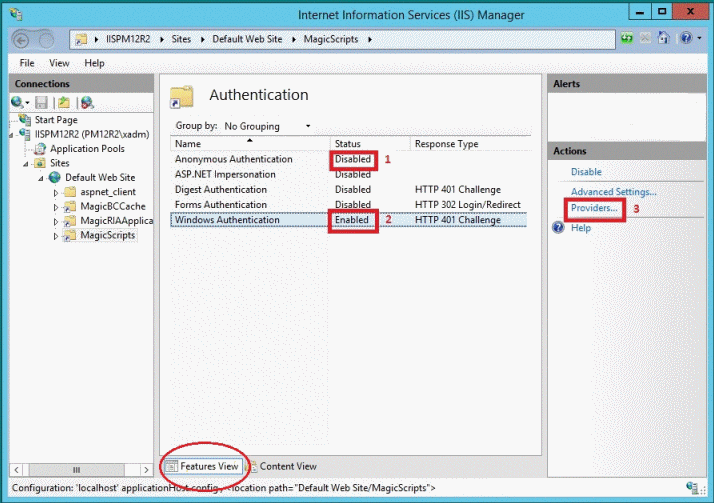
-
Right click on Anonymous Authentication and select Disabled.
-
Right click on Windows Authentication and select Enabled.
-
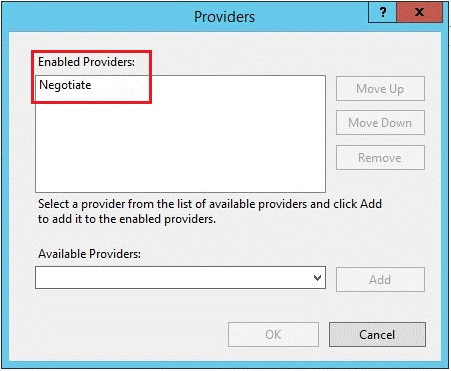
From the Actions section (right part of IIS GUI), click on the Providers option. The Providers dialog box opens.
-
Ensure that the Negotiate provider is in the Enabled Providers list, and that appears in the first row.
4. Restart IIS.
5. Forward authentication HTTP variable from the Web server machine (B) to the Magic xpa server (C).
In the Scripts\config\mgreq.ini file (for the Space middleware) or the Scripts\mgreq.ini file (for the Broker middleware), set:
HttpVars = AUTH_USER
6. Enable automatic Active Directory authentication in the Magic xpa server.
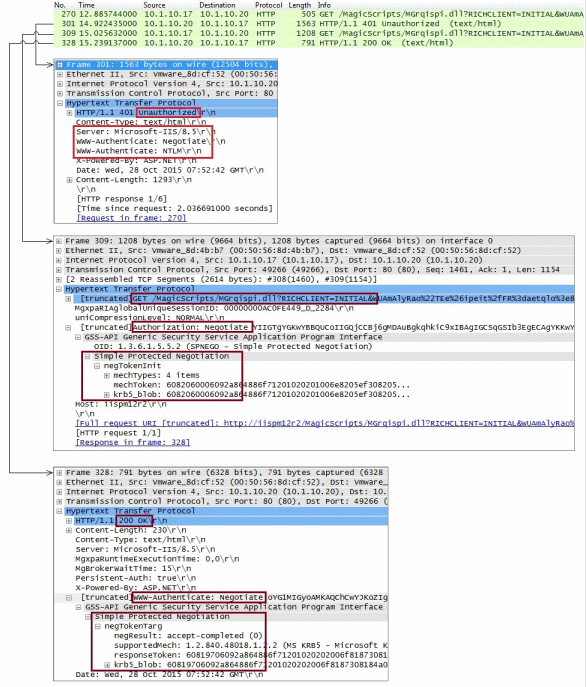
The following image depicts RIA session frames when authenticating with both Kerberos and NTLM providers allowed.
The image shows sending of the RIA's initial requests and the responses.
-
Frame 270: A RIA end user (D in the diagram above) starts the application. The RIA's initial message is sent to the IIS Web Server (B in the diagram above).
-
Frame 301: The IIS Web Server (B) rejects the message with: “HTTP Error 401 - Unauthorized: Access is denied due to invalid credentials.” In addition, the Web Server sends an Authentication negotiation proposal with Kerberos (Negotiate) and NTLM providers.
-
Frame 309: The RIA resends an initial message with authorization headers and Kerberos tickets.
-
Frame 328: The IIS Web Server (B) answered “OK” with an authentication header and Kerberos token.
Windows Server 2008 R2 introduced a new feature in IIS called Negotiable 2 or Nego2, which allows new authentication providers, such as LiveID or CardSpace to work with IIS.
One of the additional benefits of Nego2 is that it enables having a Kerberos/Negotiate authentication provider that will never fall back to NTLM if it cannot authenticate using Kerberos – this is the new Negotiate:Kerberos provider.
The downside of this is that to use Nego2 providers (including Negotiate:Kerberos), you have to disable kernel-mode authentication, which can decrease performance and cause other problems depending on your configuration.
For additional information, see: https://technet.microsoft.com/en-us/library/cc771945.aspx.

