How Do I Encrypt and Decrypt Data? (Magic xpa 3.x)
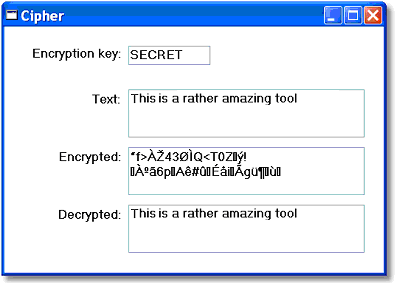
You can use the Magic xpa Cipher() and DeCipher() functions to specifically encrypt and decrypt a BLOB of data. These support specific encryption algorithms, so you can decipher data coming from other applications. The supported algorithms include both symmetric algorithms like Blowfish and asymmetric algorithms such as RSA.
Symmetric algorithms make use of the same key for encrypting and decrypting data. Other algorithms are asymmetric, and you need a key pair, one to encrypt and one to decrypt.
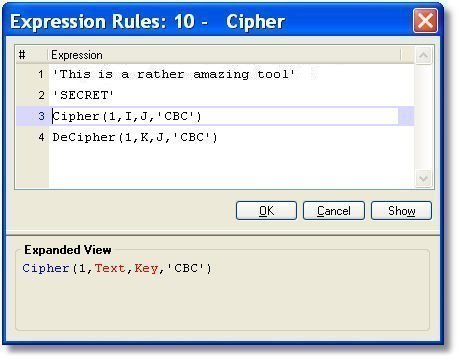
The syntax for Cipher() is:
Cipher(Cipher ID, Buffer, Key [, Mode, IV])
Where:
-
Cipher ID is a number representing which encrypting algorithm to use. In our example we used 1, which is Blowfish (See the Supported encryption methods section below).
-
Buffer is the BLOB that contains the data to encrypt.
-
Key is a BLOB containing the key. The required key length depends on which algorithm you are using. In our example our key is the word ‘SECRET’.
-
Mode is an optional parameter specifying which mode to use. The allowable modes depend on the encrypting algorithm.
-
IV is a BLOB containing an initialization vector. This parameter is also optional.
Cipher() returns a BLOB, which contains the encrypted text.
The syntax for Decipher() is identical to that of Cipher():
Decipher(Cipher ID, Buffer, Key [, Mode, IV])
Where:
-
Cipher ID is a number representing which encrypting algorithm to use. In our example we used 1, which is Blowfish (See the Supported encryption methods section below).
-
Buffer is the BLOB that contains the data to encrypt.
-
Key is a BLOB containing the key. The required key length depends on which algorithm you are using. In our example our key is the word ‘SECRET’.
-
Mode is an optional parameter specifying which mode to use. The allowable modes depend on the encrypting algorithm.
-
IV is a BLOB containing an initialization vector. This parameter is also optional.
Decipher() returns a BLOB, which contains the decrypted text.
|
Algorithm Name
|
Cipher Code
|
Supported Modes
and IV (Length in bytes)
|
Key Length (in bytes)
|
Symmetry
|
|
BLOWFISH
|
1
|
ECB - NA
CBC - 8
CFB - 8
OFB - 8
|
Supported: 1 – 56
Recommended: 16
|
Symmetric
|
|
CAST
|
2
|
ECB - NA
CBC - 8
CFB - 8
OFB - 8
|
Supported: 5 – 16
Recommended: 8
|
Symmetric
|
|
DES
|
3
|
ECB - NA
CBC - 8
CFB - 8
OFB - 8
|
Supported: 8
Recommended: 8
|
Symmetric
|
|
RC2
|
5
|
ECB - NA
CBC - 8
CFB - 8
OFB - 8
|
Supported: 5 – 16
Recommended: 8
|
Symmetric
|
|
RC4
|
6
|
Not Applicable
|
Supported: 1 – NR
Recommended: 16
|
Symmetric
|
|
RC5
|
7
|
ECB - NA
CBC - 8
CFB - 8
OFB - 8
|
Supported: 1 – 255
Recommended: 16
|
Symmetric
|
|
DES3
|
8
|
ECB3 - NA
CBC3 - 8
|
Supported: 16 and 24
Recommended: 24
|
Symmetric
|
|
RSA
|
9
|
Not Applicable
|
Supported: 48 – 2048
Recommended: 128
|
Asymmetric
|
|
AES
|
10
|
ECB - NA
CBC - 8
CFB - 8
OFB - 8
|
Supported: 16, 24, 32
Recommended: 16
|
Symmetric
|
The Online and Rich Client Samples projects (program SE01 and RSE01)

